Hexaware Strengthens Data Capabilities with Acquisition of Softcrylic Know More
This website uses cookies. By continuing to browse the site, you are agreeing to our use of cookies
Hexaware’s Guide for Databricks Unity Catalog Security: Row Level Access and Column Level Security Control
Cloud
November 15, 2024
Databricks Unity Catalog offers fine-grained access control to your datasets, ensuring holistic data security and compliance. It provides a comprehensive data governance solution with features like encryption keys, granular access controls, and audit logs.
The platform has been designed to unlock data security and compliance control regulations, making it ideal for managing sensitive datasets and workloads, such as Personal Identifiable Information (PII). You can confidently secure data using Unity Catalog while adhering to stringent regulatory requirements. A boon for businesses in dynamic markets!
This blog article will explore how Unity Catalog security can transform your data security practices. We will explore its key features, including encryption, granular access controls, audit logs, and data governance.
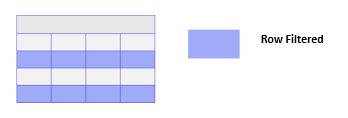
Understanding Row-Level Access Control (RLAC)
Unity Catalog’s Row-Level Access Control (RLAC) in Databricks Unity Catalog is critical for enhancing data governance and security. By allowing administrators to apply row permissions to specific users or groups, RLAC ensures that data access is tightly controlled and aligned with policies. This granular control is essential for maintaining compliance with regulatory requirements, especially when handling sensitive datasets such as Personal Identifiable Information (PII).
In data governance, RLAC helps enforce data access policies consistently. It ensures that users only see the data they are authorized to access, reducing the risk of data breaches and unauthorized access. This level of control also supports auditing and monitoring efforts, as it provides a clear trail of who accessed what data and when.
Moreover, RLAC facilitates the implementation of complex access control scenarios without compromising performance or usability. Dynamically filtering rows based on user privileges or group policies allows for more flexible and secure data sharing. This is particularly important in collaborative environments where multiple teams or departments need access to different subsets of data.
In summary, Row-Level Access Control in Databricks Unity Catalog is a powerful tool for enhancing data governance, ensuring compliance, and protecting sensitive information. It provides the framework to manage data access effectively, enabling enterprises to use data assets securely and responsibly.
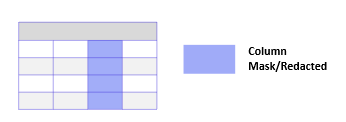
Understanding Column-Level Security Control (CLS)
Unity Catalog Column-Level Security (CLS) in Databricks Unity Catalog functions similarly to Row-Level Access Control (RLAC), but instead of limiting access to specific rows, it restricts access to specific columns. This is achieved by redacting data values or applying masking rules to ensure that sensitive information is not exposed to unauthorized users.
In the context of data governance, CLS is crucial for protecting sensitive data elements such as Social Security Numbers, credit card information, or any other Personally Identifiable Information (PII). By controlling access at the column level, you can ensure users only see the data they are permitted to view, without compromising the integrity or usability of the dataset.
Implementing CLS helps enterprises comply with various regulatory requirements, such as GDPR, HIPAA, and CCPA, which mandate stringent controls over sensitive data. It also enhances the overall security posture by minimizing the risk of data breaches and unauthorized access.
This feature takes data governance and compliance a step further when combined with RLAC. CLS and RLAC ensure that data is secure and accessible only to authorized users, providing a multi-layered approach to data security.
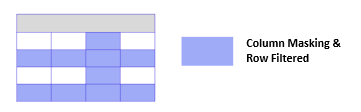
Understanding Dynamic Views
Dynamic Views in Databricks Unity Catalog are a powerful feature that generates different table data (both rows and columns) based on the user privileges of the person querying the table. This capability allows for fine-grained access control, encapsulating row-level and column-level data masking within a single configuration.
On using Dynamic Views, administrators can configure complex access-control layers that adapt dynamically to the querying user’s permissions. This means that different users can see different subsets of the data, both in terms of rows and columns, based on their specific access rights. This is particularly useful for organizations that must enforce strict data governance policies while allowing flexible data access.
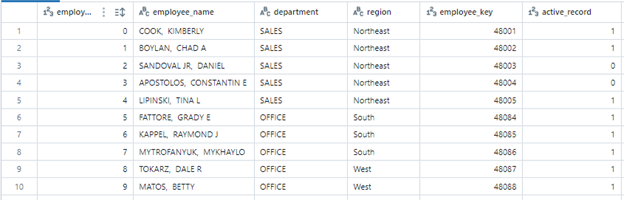
In the snapshot below, we have a data table holding various information about employees, including their associated departments, regions, and more. Let’s look at a typical example of how row and column-level data security has been applied to this table.
- Row-Level Security: Ensures that users can only see the available rows. For instance, a manager might only see the employees in their department.
- Column-Level Security: Masks or redacts sensitive data in specific columns based on user roles. For example, only HR personnel might have access to view salary information, while other users see masked values.
By using these security measures, we can safeguard sensitive information while still providing necessary data access to authorized users. This approach strengthens data governance and aligns with compliance requirements for adaptability in data management practices.
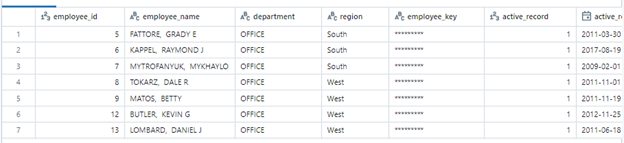
Here’s the sample employee table, before applying rules:
Create & Apply Row/Column rules
We’re using the SQL function to check whether the querying user belongs to the business group or hides the rows and masks the columns. Below are the definitions of the respective data control logic.
- Function fn_sales_identity: This function checks if a user belongs to the sales group ROLE-Sales-Team. If not, it limits access to sales rows.
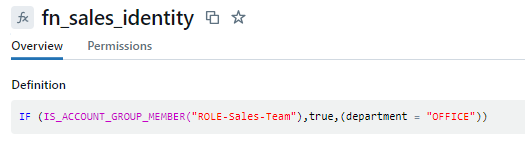
- Function employee_col_mask: This function performs a user privilege check to determine whether to expose or mask the data values in the employee_key column.
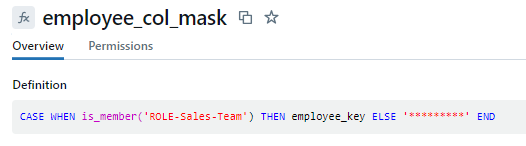
Below is the final output view when a non-sales user queries the employee table:
Conclusion
In summary, these Databricks Unity Catalog features are crucial for granular control over data access, ensuring that users only see the data they are permitted to view, thereby reducing the risk of data breaches and unauthorized access.
Furthermore, the Dynamic Views feature enhances this security by generating different table data based on user privileges, encapsulating both row-level and column-level data masking within a single configuration.
This multi-layered approach to data security ensures that enterprises can enforce strict data governance policies while still allowing flexible data access. For more information on how to filter sensitive table data using row filters and column masks, explore the options available on Azure, AWS, and GCP.
If you would prefer the guidance of an expert, Hexaware’s data and AI team can develop comprehensive frameworks for your team to utilize Unity Catalog effectively, while also supporting you in adopting best practices with Databricks. Learn more about our Data & AI services here.
About the Author
Vignesh Ramachandran
Vignesh is a seasoned data lead with over a decade of experience in diverse cloud technology stacks, with a specialization in Databricks and Spark-based solutions. He excels in productionizing data and developing ETL solutions on the Azure Cloud platform. He also has strong expertise in solution architecture, business insights, and technical leadership.
Read more








